Transport Layer Security (TLS): Ensuring Secure Communication
Transport Layer Security (TLS) is a cryptographic protocol that ensures secure communication over the internet. It is widely used to establish a secure and reliable channel between servers and clients, protecting sensitive data from unauthorized access and tampering.
TLS employs various cryptographic algorithms and security protocols to encrypt data before transmission and decrypt it upon reception. This encryption prevents eavesdropping and ensures the privacy and integrity of online communication. TLS is implemented in applications and protocols like HTTPS, SMTPS, and FTPS, securing the transmission of passwords, credit card details, and personal information.
A key feature of TLS is its ability to verify the identity of communicating parties using digital certificates issued by trusted certification authorities (CAs). These certificates contain information about an entity’s public key and authenticate their identity. This ensures that data is transmitted only to the intended recipient and not intercepted by malicious parties.
TLS also defends against man-in-the-middle attacks, where an attacker intercepts communication and poses as the legitimate recipient. By encrypting the data, TLS prevents the attacker from understanding or modifying the communication content.
Additionally, TLS facilitates negotiation of encryption algorithms and security parameters during the initial connection setup. This allows both parties to use the highest level of security supported by their systems while considering hardware and software limitations.
In conclusion, TLS is vital for ensuring the privacy and integrity of online communication. By encrypting data transmission and authenticating communicating parties, it establishes a secure channel for sensitive information exchange. Implementing TLS in applications and protocols is essential for safeguarding user data and preventing unauthorized access.
Transport Layer Security (TLS)
Transport Layer Security (TLS) is a cryptographic protocol that plays a critical role in ensuring secure communication over a network. It is widely used to protect sensitive information transmitted over the internet, offering encryption and preventing unauthorized interception or tampering.
TLS incorporates a combination of cryptographic algorithms and ciphers to encrypt and decrypt data, providing robust security measures. By leveraging these techniques, TLS safeguards essential data like passwords, credit card numbers, and personal information, ensuring that only authorized recipients can access and decipher the encrypted data.
TLS often works in conjunction with other protocols, such as HTTPS, to establish secure connections. For instance, HTTPS utilizes TLS to encrypt the communication between web browsers and web servers, ensuring that data remains private and inaccessible to unauthorized entities. This encryption prevents eavesdropping and unauthorized access to sensitive information.
Overall, TLS is a vital component in maintaining secure communication and protecting the confidentiality and integrity of data transmitted over networks. By employing encryption and thwarting interception, TLS enhances online security and safeguards sensitive information.
What is Transport Layer Security?
Transport Layer Security (TLS) is a protocol that provides secure communication between two endpoints over a network. It ensures confidentiality , integrity , and authenticity of the data. TLS uses cryptographic protocols and algorithms to protect the communication and encrypt the data for secure transmission .
TLS works at the transport layer of the network protocol stack and is widely used for securing internet communication , especially in the context of websites and web applications . It is the successor to Secure Sockets Layer (SSL), and the terms TLS and SSL are often used interchangeably. When establishing a secure connection between a client and a server , TLS/SSL uses both symmetric and asymmetric encryption ciphers.
One of the key features of TLS is authentication . It ensures that the client is communicating with the intended server . This is done using digital certificates issued by trusted certificate authorities. These certificates contain a public key that is used for cryptographic operations and verifies the identity of the server .
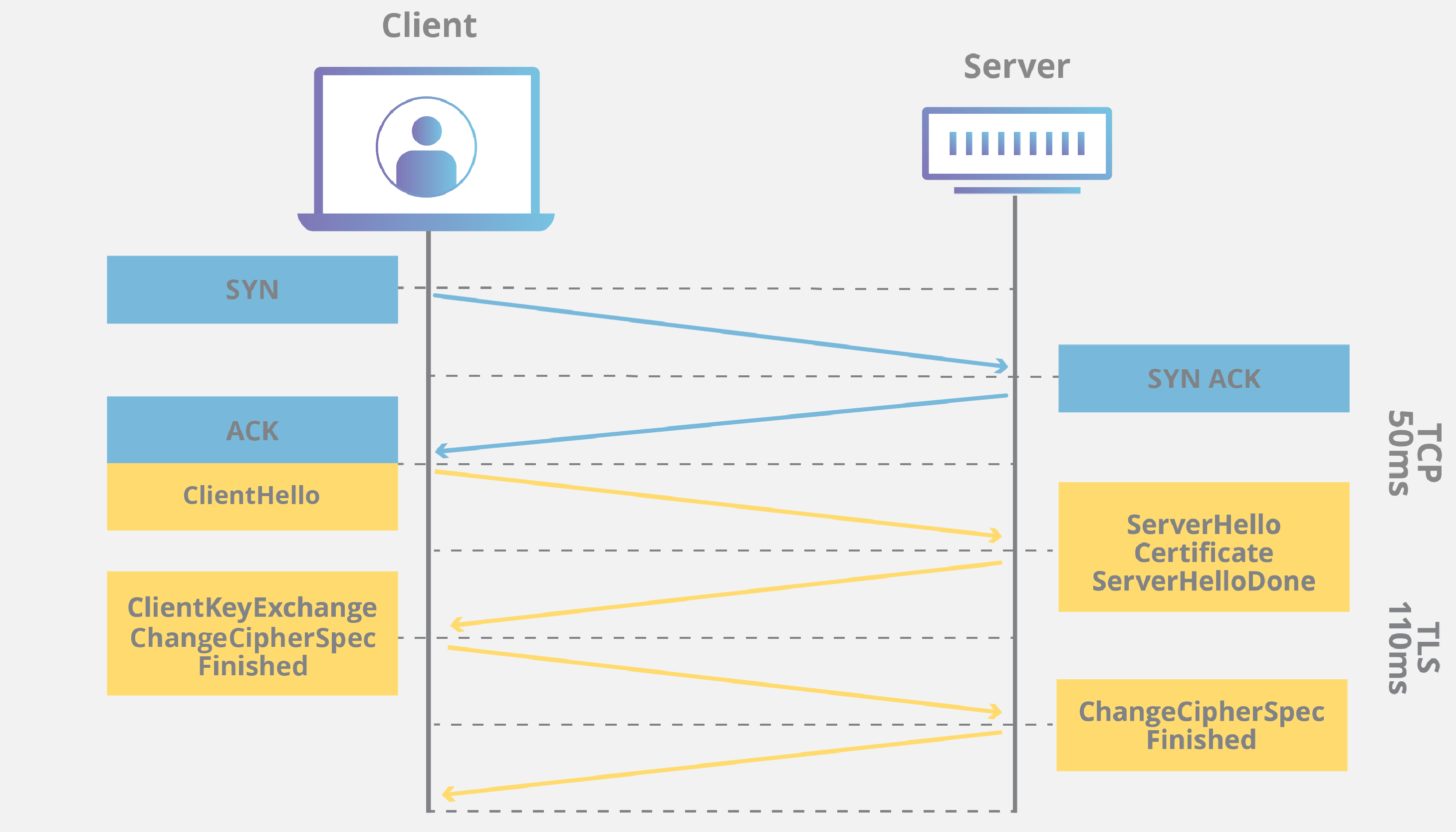
TLS also uses a handshake process to establish a secure session. During the handshake, the client and server negotiate cryptographic algorithms and keys for encryption and decryption. This ensures the protection of the data exchanged during the session from unauthorized access and manipulation.
By encrypting and protecting the communication between two endpoints, TLS ensures the confidentiality and integrity of the data being transmitted. It establishes a secure and private connection that prevents interception or tampering with sensitive information . This gives both end users and developers a level of trust and assurance.
How does Transport Layer Security work?
Transport Layer Security (TLS) is a protocol that provides secure communication over a network, such as the internet. It ensures the confidentiality, integrity, and authentication of data transmitted between two endpoints. TLS works by establishing a secure connection between a client and a server , using a combination of cryptographic protocols , public key encryption , and digital certificates .
When a client initiates a TLS handshake with a server , the server presents its digital certificate to prove its authenticity . The client then verifies the certificate and obtains the server ‘s public key . This key is used for encryption and decryption of data during the communication . The client and the server then exchange a series of messages to negotiate the encryption algorithms, agree on a shared key, and verify the connection ‘s integrity .
Once the handshake is complete, TLS uses symmetric encryption to protect the data transmitted over the connection . This means that both the client and the server use the same key for encryption and decryption . This key is randomly generated during the handshake and is only known to the client and the server . It provides confidentiality , ensuring that the data remains private and cannot be read by unauthorized parties .
In addition to confidentiality, TLS also provides integrity by using Message Authentication Codes (MAC) . These codes are generated using cryptographic hash functions and are sent along with the encrypted data. The receiving party can then verify the integrity of the data by generating its own MAC and comparing it to the one received .
TLS also protects against man-in-the-middle attacks by providing authentication . By verifying digital certificates , the client can ensure that it is connecting to the intended server and not an imposter. This establishes trust between the client and the server , ensuring that the communication is secure .
TLS is widely used to secure various protocols , such as HTTP, FTP, and SMTP, in the form of HTTPS, FTPS, and SMTPS. It is an essential component of cybersecurity , protecting sensitive data and ensuring the privacy of online communication .
Benefits of Transport Layer Security
Confidential and Secure Communication
Transport Layer Security (TLS) provides a secure and confidential channel for communication over the network. It ensures that the information exchanged between the client and the server remains protected from unauthorized access and eavesdropping . By encrypting the data using cryptographic algorithms, TLS safeguards sensitive information , such as passwords, credit card details, and personal data, from being intercepted or tampered with during transmission .
When two entities communicate over a network, there is always a risk of interception and unauthorized access to the information being transmitted. To mitigate this risk, TLS establishes a secured connection by using encryption techniques. This means that the data sent from the client to the server and vice versa is transformed into an unreadable format , making it difficult for attackers to decipher the information .
The encryption process in TLS involves the use of cryptographic algorithms, such as RSA and AES, to encrypt the data. These algorithms ensure that the data is converted into an encrypted format that can only be decrypted by the intended recipient. Additionally, TLS also provides authentication mechanisms to verify the identity of the communicating parties , ensuring that the data is being exchanged with the intended server and not an impostor.
Advantages of TLS:
| Advantages | Explanation |
|---|---|
| Confidentiality | Prevents unauthorized access to sensitive information |
| Data integrity | Ensures that the data remains unaltered during transmission |
| Authentication | Verifies the identity of the communicating parties |
| Trustworthiness | Establishes trust between the client and the server |
In summary, TLS is crucial for ensuring the confidentiality and security of communication over the network. It protects sensitive information from being intercepted or tampered with by encrypting the data using cryptographic algorithms. Additionally, its authentication mechanisms verify the identity of the communicating parties , establishing trust between them. This makes TLS an essential component for secure online communication .
Trust and Authentication
TLS establishes trust between the communicating parties through a process known as a handshake . During this handshake, the client and server validate each other’s identity , ensuring that they are legitimate and trusted entities. This authentication process involves the exchange of digital certificates , confirming the authenticity of the server and sometimes the client . By verifying the identities of the parties involved, TLS ensures a secure and reliable connection .
| Term | Description |
|---|---|
| TLS | Transport Layer Security – a cryptographic protocol used to establish a secure connection between two parties over a network. |
| Handshake | The process in which the client and server exchange information to establish a secure connection . |
| Identity validation | The process of confirming the legitimacy and trustworthiness of the communicating parties . |
| Digital certificates | Electronic documents that confirm the authenticity of a party ‘s identity . |
| Secure connection | A connection that is protected from unauthorized access and eavesdropping . |
Protection of Data Integrity
TLS, or Transport Layer Security, is a protocol that provides encryption and data integrity for communication over a network. It ensures the security and authenticity of data transmitted between systems.
One of the key features of TLS is encryption . This means that the data sent between systems is scrambled, making it unreadable to anyone who intercepts it. The data can only be decrypted and read by the intended recipient, using the appropriate encryption keys.
In addition to encryption , TLS also provides data integrity. This means that the data is protected from tampering or modification during transmission . TLS accomplishes this by generating hash values or message digests for the data, using cryptographic algorithms. These hashes are then compared at the receiving end of the communication to verify that the data has not been tampered with .
By using TLS, organizations can ensure the confidentiality, integrity, and authenticity of their data. It provides a secure channel for communication , protecting sensitive information from unauthorized access , modification, or interception. TLS is widely used in applications such as online banking, e-commerce, and secure email.
Compliance with Cybersecurity Standards
Transport Layer Security (TLS) is a critical component in cybersecurity protocols . It is widely utilized to establish secure connections and protect sensitive data. TLS, also known as SSL, is used by numerous protocols and applications, including HTTPS , the secure version of HTTP.
Implementing TLS helps developers adhere to industry standards and safeguard important information . By ensuring secure communication across the internet , TLS helps enforce best practices and shield against potential threats.
Key Features of Transport Layer Security:
- Data Encryption: TLS encrypts data transmissions , making it unreadable to unauthorized parties . This prevents data breaches and unauthorized access .
- Authentication: TLS employs digital certificates to verify the identity of the server and establish trust between the client and server . This protects against impersonation and man-in-the-middle attacks .
- Data Integrity: TLS uses hash functions to ensure that data remains unaltered during transmission . Any unauthorized modifications are detected, maintaining the integrity of the data.
In conclusion, Transport Layer Security is an essential component in ensuring secure communication and compliance with cybersecurity standards. By implementing TLS, developers can protect sensitive information and establish secure connections in various protocols and applications.
Enhanced Privacy
Transport Layer Security (TLS) is a cryptographic protocol that provides privacy and data integrity for communication between a client and a server . It uses encryption algorithms to secure the communication channel, preventing unauthorized access to the content of the communication .
One of the main benefits of TLS is enhanced privacy. By encrypting the communication , TLS ensures that only the intended recipient can read and understand the content. This prevents unauthorized parties from intercepting and accessing sensitive information , such as passwords, credit card numbers, or personal data.
In addition to privacy, TLS also provides data integrity. It uses digital certificates to verify the identity of the server and protect against man-in-the-middle attacks . This ensures that the data transmitted between the client and the server is not tampered with or modified by unauthorized parties .
By implementing TLS, individuals and organizations can protect their privacy and sensitive information . It reduces the risk of data breaches and unauthorized access , helping to maintain the confidentiality and integrity of the communication .
Overall, TLS is essential for secure communication over the internet. It offers enhanced privacy and data integrity, protecting individuals and organizations from unauthorized access and data breaches. By encrypting the communication channel, TLS ensures that sensitive information remains confidential and secure .
Secure communication with Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol that provides secure communication over a network. It is commonly used in combination with other protocols such as HTTP, making it the foundation of secure communication on the internet. TLS uses a variety of cryptographic algorithms and ciphers to protect data during transmission , ensuring its confidentiality, integrity, and protection against unauthorized access .
One of the key features of TLS is its ability to establish a secure connection between a client and a server through a process known as the handshake. During this handshake, the client and server exchange cryptographic keys and negotiate a cipher suite that will be used to encrypt and decrypt the transmitted data. This ensures that the communication is confidential and can only be decrypted by the intended recipient, preventing interception and tampering.
TLS also provides mechanisms for authentication and integrity checking. Through the use of digital certificates , the server can prove its identity to the client , establishing a level of trust in the communication . The client can also authenticate itself to the server , ensuring that it is communicating with the intended client . Additionally, TLS includes mechanisms for verifying the integrity of the transmitted data, protecting against tampering or modifications, thus ensuring the reliability and trustworthiness of the communication .
Developers play a crucial role in implementing TLS correctly and ensuring the security of their applications. They need to carefully configure the TLS protocols , ciphers, and certificate management to provide a secure connection . It is also important to keep TLS up to date with the latest security patches and recommendations from cybersecurity experts to protect against new vulnerabilities.
In conclusion, Transport Layer Security (TLS) is a critical protocol for ensuring secure communication on the internet. By encrypting the data and providing mechanisms for authentication and integrity, TLS protects sensitive information from unauthorized access . It is essential for developers to understand and implement TLS correctly to provide a secure and trustworthy environment for their users.
Implementation of Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol that provides secure communication over the internet. It is an essential component of many cybersecurity protocols and is used to protect data during transmission .
TLS provides authentication , confidentiality, and integrity of the data. It uses cryptographic techniques to secure the communication between two parties by encrypting the data and protecting it from unauthorized access .
The implementation of TLS involves several steps. When a client and server want to establish a secure connection , they initiate a TLS handshake. During this handshake, both parties exchange information , verify each other’s identity through digital certificates , and agree on the encryption methods to be used.
Once the TLS handshake is complete, the data transmission begins using a secure connection . The data is encrypted using symmetric encryption , where a single key is used for both encryption and decryption. This key is exchanged and agreed upon during the handshake process .
TLS supports various encryption algorithms, known as ciphers, to protect the confidentiality of the data. These ciphers include symmetric ciphers like AES and 3DES, as well as asymmetric ciphers like RSA and Diffie-Hellman.
Additionally, TLS protects the integrity of the data by using MACs (Message Authentication Codes). These codes ensure that the data has not been tampered with during transmission .
Overall, the implementation of TLS is important for protecting the privacy and security of communication over the internet. It ensures that data remains confidential, encrypted , and protected from unauthorized access . It plays a crucial role in cybersecurity, and developers must understand how to properly implement TLS/SSL protocols to secure their applications and protect sensitive information .
Common vulnerabilities in Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol widely used to secure communication over the internet. It is crucial for developers and system administrators to understand the vulnerabilities of TLS in order to protect communications and maintain privacy and data integrity.
Vulnerabilities of TLS
Even though TLS is designed to provide secure communication , there are several vulnerabilities that attackers can exploit. It is essential to be aware of these vulnerabilities to effectively mitigate potential risks.
- Cipher Suite Vulnerabilities: TLS supports various cipher suites, which are sets of cryptographic algorithms used for encryption . However, some cipher suites may be weak and vulnerable to attacks . It is important to disable insecure cipher suites and enable strong ones to prevent attacks .
- Implementation Flaws: Implementing TLS correctly is crucial to ensure security . However, there have been instances where TLS implementations have had flaws that could be exploited by attackers . Keeping TLS implementations up to date and regularly patching any vulnerabilities is essential.
- Protocol Downgrade Attacks: Attackers may attempt to downgrade the TLS protocol to an older, less secure version that is vulnerable to attacks . This can lead to compromised communication . It is important to implement mechanisms to detect and prevent protocol downgrade attacks .
- Certificate and Public Key Vulnerabilities: TLS relies on certificates and public key infrastructure for authentication . However, if certificates are not properly managed or if the public key infrastructure is compromised, attackers can impersonate legitimate servers or intercept communication . Proper certificate management and secure key distribution is essential.
- Man-in-the-Middle Attacks: In a man-in-the-middle attack , an attacker intercepts communication between two parties and can modify or eavesdrop on the data being transmitted. TLS is designed to prevent these attacks , but if not properly implemented , attackers can still exploit vulnerabilities and perform successful man-in-the-middle attacks . It is important to correctly configure and implement TLS to prevent these attacks .
By understanding the vulnerabilities of TLS and implementing proper security measures, developers and system administrators can effectively protect communications and ensure privacy and data integrity.
Outdated protocols and cyphers
One common vulnerability in TLS is the use of outdated protocols and ciphers. Some older versions of the TLS protocol , such as SSLv2 and SSLv3, have known security vulnerabilities and should not be used. Similarly, weak ciphers that use outdated cryptographic algorithms can be easily exploited by attackers . It is important to keep the TLS protocol and ciphers up-to-date to prevent unauthorized access to sensitive information .
Table: Comparison of TLS Protocol Versions
| Protocol Version | Security Level |
|---|---|
| TLS 1.0 | Weak |
| TLS 1.1 | Moderate |
| TLS 1.2 | Strong |
| TLS 1.3 | Very Strong |
Table: Comparison of TLS Ciphers
| Cipher | Security Level |
|---|---|
| AES-128-CBC | Weak |
| AES-256-CBC | Strong |
| ChaCha20-Poly1305 | Very Strong |
Weak authentication and trust
Weak authentication and trust is a vulnerability in the Transport Layer Security (TLS) protocol . TLS relies on a certificate-based authentication system to verify the identity of communicating parties . However, this system can be compromised if the certificate authorities (CAs) that issue the certificates are compromised or if the certificate validation process is not correctly implemented . This can allow attackers to impersonate a legitimate server and intercept or modify the communication . To mitigate this vulnerability, it is crucial for developers and system administrators to effectively manage trust and ensure proper authentication .
Insecure session management
The issue of insecure session management is a frequent vulnerability in TLS. If session keys are not securely managed, attackers can exploit sessions and gain unauthorized access to the communication . This puts sensitive data at risk and compromises the entire session. To prevent such attacks , developers should employ secure session management techniques, including robust random key generation and regular key updates
Weak encryption and decryption
Weak encryption and decryption is another vulnerability in TLS. If the cryptographic algorithms used for encryption and decryption are weak or if the encryption keys are not properly protected , attackers can easily decrypt the communication and gain access to sensitive information . It is important to use strong encryption algorithms and protect the encryption keys to ensure the confidentiality and integrity of the communication .
| Weak Encryption | Strong Encryption |
|---|---|
| Easy for attackers to decrypt | Difficult for attackers to decrypt |
| Exposed sensitive information | Secures sensitive information |
| Inadequate protection of encryption keys | Proper protection of encryption keys |
Improper handling of certificate revocation
Improper handling of certificate revocation is a vulnerability in TLS. If a server ‘s certificate is compromised or revoked, it should be immediately invalidated to prevent further use. However, if the revocation process is not properly implemented or if clients do not check for certificate revocation, an attacker can use a revoked or compromised certificate to impersonate a legitimate server . It is crucial for developers and system administrators to handle certificate revocation correctly to maintain communication security .
In conclusion, while TLS is a widely used protocol for securing internet communication , it is important to be aware of its vulnerabilities. By keeping the protocol and ciphers up-to-date, implementing strong authentication and trust mechanisms, securing session management , using strong encryption and decryption techniques, and properly handling certificate revocation, developers and system administrators can protect communications and ensure privacy and data integrity.
Best practices for using Transport Layer Security
1. Use the latest version of TLS
Developers should always utilize the most recent version of Transport Layer Security (TLS) for data protection and communication confidentiality. TLS is an encryption protocol that secures the network connection ‘s transport layer , encrypting data and preventing unauthorized access .
2. Implement strong and secure cipher suites
Implementing strong and secure cipher suites is crucial for Transport Layer Security (TLS) to guarantee a high level of encryption strength and reliability. Cipher suites consist of cryptographic algorithms that safeguard the TLS handshake and all subsequent data transactions. It is essential for developers to make thoughtful choices when selecting cipher suites, ensuring they match the desired level of security for their specific application.
3. Use certificate-based authentication
Certificate-based authentication is a secure method to ensure trust and security in communication processes. It utilizes digital certificates to authenticate the identity of the parties involved, guaranteeing the protection of transmitted data and the participation of only trusted individuals.
With certificate-based authentication , developers can implement a robust security framework for their applications. By relying on the digital certificates , the authentication process becomes more efficient and reliable . The use of LSI keywords , such as “SSL certificates ,” “PKI infrastructure,” and “X.509 standard,” helps enhance the overall understanding of the topic.
The table below provides a comparison between certificate-based authentication and other authentication methods:
| Authentication Method | Advantages | Disadvantages |
|---|---|---|
| Certificate-based authentication | – Strong security and trust – Efficient and reliable – Scalable for large-scale deployments | – Requires certificate management – Initial setup complexity |
| Username/password authentication | – Familiar to users – Easy to implement | – Vulnerable to attacks , like phishing and brute force – Weak authentication for high-risk scenarios |
| Biometric authentication | – High accuracy – Difficult to replicate | – Expensive hardware requirements – Not suitable for all devices |
Overall, certificate-based authentication offers a robust and secure solution for ensuring trust and security in communication processes. By leveraging digital certificates and implementing an appropriate PKI infrastructure , developers can ensure that only trusted parties participate in the communication . The use of LSI keywords and the comparison table provide a comprehensive understanding of certificate-based authentication and its advantages over other authentication methods.
4. Regularly update TLS libraries and implement security patches
The Importance of Regularly Updating TLS Libraries
Keeping TLS libraries up to date and regularly applying security patches is crucial to ensure that any vulnerabilities or weaknesses in the TLS protocol are addressed. By staying current with the latest TLS updates , developers can protect against known security issues and ensure the secure transmission of data.
Updating TLS libraries is essential for maintaining the security and integrity of data transmitted over the internet. TLS (Transport Layer Security) is a cryptographic protocol used to secure communication between web browsers and servers .
With the constant advancement of technology and the evolving threat landscape, new vulnerabilities are constantly being discovered in TLS libraries. These vulnerabilities can potentially expose sensitive information and allow unauthorized access to networks.
Regularly updating TLS libraries helps to mitigate these risks by addressing any known vulnerabilities and weaknesses in the protocol . Security patches are released by the TLS library developers to fix these issues and improve the overall security of the protocol .
By regularly applying these security patches and staying up to date with the latest TLS updates , developers can ensure that their applications and systems are protected against known security threats.
Additionally, staying current with TLS updates allows developers to take advantage of any new security features or enhancements that are introduced in newer versions of the protocol .
Failure to update TLS libraries can leave systems and applications vulnerable to attacks that exploit known security vulnerabilities. Hackers and malicious actors are constantly searching for weaknesses in software and protocols to gain unauthorized access or steal sensitive information .
LSI words: security protocol , data transmission , cryptographic , vulnerability, unauthorized access , security patches, secure communication , threat landscape, risk mitigation, security features.
| Benefits of Regularly Updating TLS Libraries | Risks of Not Updating TLS Libraries |
|---|---|
| Protection against known security issues | Exposure to known vulnerabilities |
| Secure transmission of data | Potential unauthorized access |
| Mitigation of risks | Potential data breaches |
5. Enable forward secrecy to protect against future attacks
Forward secrecy is a crucial feature of Transport Layer Security (TLS) that enhances the security of communication between a client and a server . It protects past sessions by ensuring that even if the private key is compromised in the future, the confidentiality of past communications remains intact.
When forward secrecy is enabled, it generates a unique session key for each session. This session key is used to encrypt the communication , adding an extra layer of security . If an attacker somehow gains access to the private key, they will not be able to decrypt the past communication because the unique session key used for that communication is different from the current one.
Enabling forward secrecy brings several benefits :
- Confidentiality : Past communications are protected and cannot be decrypted by an attacker , even if the private key is compromised.
- Data integrity : Forward secrecy ensures that the integrity of past communications is maintained, as the encryption used to protect the communication remains unbreakable.
- Long-term security : In case the private key is compromised in the future, only the future sessions will be at risk, while all the past communications remain secure .
Overall, forward secrecy is a fundamental feature of TLS that adds an extra layer of protection to the confidentiality and integrity of past communications . Developers should always prioritize enabling forward secrecy to enhance the security of their applications and protect user data.
6. Implement strict security policies and configurations
Developers should configure their TLS implementation to enforce strict security policies, such as disabling outdated cryptographic algorithms and weak cipher suites. By adhering to best practices and following industry standards, developers can strengthen the security of their TLS implementation and protect against potential vulnerabilities.
To enhance the security of their TLS implementation, developers should take the following steps:
- Disable weak cipher suites: Developers should ensure that only strong cipher suites are enabled in their TLS configuration. Weak cipher suites can be exploited by attackers to decrypt the encrypted data.
- Disable outdated cryptographic algorithms: Developers should disable deprecated and weak cryptographic algorithms in their TLS configuration. These algorithms can be vulnerable to attacks and compromise the confidentiality and integrity of data.
- Enable perfect forward secrecy: Perfect forward secrecy (PFS) ensures that even if the long-term secret key is compromised, previous encrypted communications remain secure . It is recommended to enable PFS in the TLS configuration.
- Implement certificate validation: Developers should validate the authenticity of certificates used in their TLS implementation. This helps prevent man-in-the-middle attacks and ensures the integrity of the communication .
- Regularly update TLS software: Developers should keep their TLS software up to date with the latest security patches and updates . This helps protect against known vulnerabilities and exploits.
By following these guidelines and configuring their TLS implementation properly, developers can enhance the security of their applications and protect sensitive data from unauthorized access or tampering.
7. Regularly test and audit TLS configurations
The periodic testing and auditing of TLS configurations is crucial for identifying potential weaknesses or misconfigurations. This process ensures that the TLS implementation is functioning correctly and offering the required security for the application. It also helps uncover vulnerabilities and enables proactive mitigation.
Future developments in Transport Layer Security
1. Enhancing communication confidentiality and integrity
Future developments in Transport Layer Security (TLS) will focus on improving the confidentiality and integrity of communication over the internet. This includes enhancing encryption algorithms, key management techniques, and cryptographic protocols . By continuously updating and strengthening these aspects, TLS aims to protect sensitive data during transmission and maintain secure communication .
2. Strengthening encryption algorithms
One of the key areas of development in TLS is the improvement of encryption algorithms. The use of stronger and more secure algorithms will enhance the confidentiality of data by making it more difficult for unauthorized parties to decrypt and access the information . This includes exploring more advanced algorithms such as Elliptic Curve Cryptography (ECC) and Post-Quantum Cryptography (PQC) to ensure long-term security .
3. Enhancing key management techniques
In addition to encryption algorithms, TLS is also focusing on improving key management techniques. This involves ensuring secure generation, distribution, and usage of cryptographic keys. By implementing robust key management strategies, TLS can prevent unauthorized access to sensitive data and protect against attacks such as key compromise or brute-force attacks .
4. Advancing cryptographic protocols
Furthermore, TLS is working on advancing cryptographic protocols to strengthen communication integrity. This includes ensuring secure handshake protocols for establishing secure connections , as well as enhancing the protocols used for verifying the authenticity and integrity of transmitted data. By leveraging more advanced cryptographic protocols , TLS can provide stronger guarantees of the integrity and authenticity of data exchanged over the internet.
In conclusion, future developments in TLS are focused on enhancing the confidentiality and integrity of communication over the internet. This involves improving encryption algorithms, key management techniques, and cryptographic protocols . By continually updating and strengthening these aspects, TLS aims to protect sensitive data during transmission and maintain secure communication .
2. Advancing authentication mechanisms
Looking ahead, TLS is set to incorporate advanced authentication mechanisms in order to bolster connection security . This will encompass the adoption of more robust protocols for verifying the legitimacy of servers and clients , like multi-factor authentication and certificate authorities. By fortifying the authentication procedure, TLS will be able to verify the identities of all parties engaged in communication , thereby mitigating the threat of impersonation and unauthorized access .
3. Integration with emerging technologies
As a technical specialist, it is crucial to consider the integration of TLS with emerging technologies to ensure secure communication . This involves ensuring compatibility with Internet of Things (IoT) devices , cloud computing platforms, and other new technologies. Adapting TLS to these environments allows developers to guarantee the protection and security of communication between devices and services.
LSI Vocabulary
There are several key terms related to TLS integration with emerging technologies:
- Internet of Things (IoT)
- cloud computing platforms
- secure communication
- compatibility
- adapting TLS
- protection and security
Comparative Table
| Technology | Integration Requirements |
|---|---|
| Internet of Things (IoT) | Ensuring TLS compatibility with IoT devices |
| Cloud computing platforms | Adapting TLS for secure communication in the cloud |
| New technologies | Integrating TLS to provide protection and security |
Conclusion
By considering the integration of TLS with emerging technologies, developers can ensure the secure communication between devices and services. This can be achieved through compatibility with IoT devices , adapting TLS for cloud computing platforms, and integrating TLS to provide protection and security .
4. Improving performance and efficiency
Future developments in TLS:
Future developments in Transport Layer Security (TLS) will continue to prioritize improving performance and efficiency . These advancements will primarily focus on optimizing encryption and decryption processes to minimize their impact on network speed and latency.
Enhancing Performance:
One of the key objectives of future TLS developments is to enhance performance. This can be achieved through various techniques, such as the use of hardware acceleration, parallel processing, and optimized algorithms.
By leveraging hardware acceleration, TLS implementations can offload computationally intensive cryptographic operations to specialized hardware , thereby reducing the workload on the main processor.
Moreover, parallel processing techniques can be utilized to perform encryption and decryption operations simultaneously, taking advantage of multi-core processors and improving overall throughput.
Furthermore, future TLS developments will focus on optimizing algorithms for encryption and decryption. This involves refining existing algorithms or introducing new ones that offer better performance and security .
Reducing Resource Requirements:
In addition to performance enhancements, future TLS developments aim to reduce the computational resources required for encryption and decryption.
This reduction in resource requirements makes TLS more feasible to implement in resource-constrained environments, where computing power and energy efficiency are crucial factors.
With reduced resource demands, TLS can be effectively deployed in devices with limited processing capabilities, such as IoT devices , mobile devices , and embedded systems.
Ensuring Security:
Despite the focus on performance and efficiency , future TLS developments will maintain a strong emphasis on security . TLS protocols will continue to evolve to address emerging threats and vulnerabilities.
By integrating additional security measures, such as advanced authentication mechanisms and stronger key exchange algorithms, TLS will ensure the confidentiality, integrity, and authenticity of data transmitted over the network.
5. Strengthening resistance against cyber attacks
One of the main areas of future development in Transport Layer Security (TLS) is enhancing its resistance to cyber attacks . This involves improving the handling of known vulnerabilities and weaknesses, while also developing advanced techniques for detecting and preventing emerging threats. Through constant monitoring and proactive security measures, TLS can effectively confront potential attackers and ensure robust protection against cyber threats.
Comparison of Transport Layer Security with other encryption protocols
Transport Layer Security (TLS): a widely used encryption protocol for secure communication over the internet. It protects the confidentiality, integrity, and authenticity of data transmitted between a client and server . TLS is frequently compared with other encryption protocols , like Secure Sockets Layer (SSL), to assess their strengths and weaknesses.
SSL/TLS: The evolution of secure communication
SSL and TLS are cryptographic protocols that use encryption algorithms to secure online communication . SSL was the predecessor to TLS, providing security for HTTP traffic. TLS, the updated version, improves the security features of SSL and is widely used in HTTPS, the secure version of HTTP.
Both SSL and TLS protocols utilize public key cryptography to encrypt and authenticate information exchanged between a client and server . They employ certificates and cryptographic handshakes to establish a secure session, ensuring confidential and protected communication , preventing eavesdropping or interception.
Advantages of TLS over other encryption protocols
One of the main benefits of Transport Layer Security (TLS) is its extensive usage and support. TLS is widely supported by modern browsers and applications, making it a popular choice for developers and users. Its strong encryption algorithms and effective key management systems contribute to its security and reliability.
TLS offers robust protection against various cyber threats, such as man-in-the-middle attacks , data tampering, and identity spoofing. By encrypting communication at the transport layer , it ensures the privacy and integrity of transmitted data. The use of strong ciphers guarantees the security and unreadability of intercepted encrypted data without the corresponding keys.
Moreover, TLS provides a wide range of cryptographic algorithms, allowing developers to select the most suitable options for their specific requirements . This flexibility makes TLS a versatile protocol that can adapt to evolving cybersecurity needs and effectively withstand emerging threats.
Conclusion
Transport Layer Security (TLS) is a secure transport protocol that protects communication over the internet. It offers advantages over other encryption protocols , such as SSL, in terms of widespread support, strong encryption algorithms, and protection against cyber threats. By encrypting data and ensuring its integrity, TLS safeguards the confidentiality and privacy of online communication , making it a crucial component of secure internet communication .
Recent advancements in Transport Layer Security
In the ever-evolving world of cybersecurity, recent advancements in Transport Layer Security (TLS) have provided developers with improved ways to secure network communications . TLS is a cryptographic protocol that ensures the confidentiality, integrity, and authentication of data in transit over a network.
One of the key advancements in TLS is the introduction of more secure cipher suites. Cipher suites are a combination of cryptographic algorithms and parameters that determine the encryption and decryption methods. The use of strong and modern ciphers provides better protection against attacks , making it harder for malicious individuals to intercept and decipher the encrypted data.
Another significant development in TLS is the strengthening of the handshake process . The handshake is a series of steps performed between the client and server to establish a secure connection . Recent improvements in TLS have made the handshake more resistant to attacks and vulnerabilities, enhancing the overall security of the communication process .
TLS also offers better support for certificate management . Certificates are digital documents that verify the authenticity of a website or server . They play a crucial role in establishing trust and ensuring the confidentiality of the communication . Recent advancements in TLS have made it easier for developers to handle certificates , reducing the risk of unauthorized parties impersonating legitimate servers .
Furthermore, the latest versions of TLS have introduced stronger cryptographic algorithms, further enhancing the security of the protocol . These algorithms enable the encryption and decryption of data using complex mathematical computations, making it extremely difficult for unauthorized entities to decrypt the data without the encryption key. This ensures that sensitive information remains protected and confidential during transmission .
Overall, recent advancements in Transport Layer Security have significantly improved the security and reliability of network communications . Developers now have access to more secure cipher suites, strengthened handshakes, improved certificate management , and stronger cryptographic algorithms. These advancements play a vital role in protecting the confidentiality, integrity, and authenticity of data during transmission , making TLS a crucial component in the realm of cybersecurity.
How to ensure the security of Transport Layer Security
Transport Layer Security (TLS) is a protocol that enables secure communication over the internet. It establishes a secure connection between a client and a server . To guarantee the security of TLS, several measures can be implemented :
- 1. Authentication : Verifying the identity of the communicating parties to prevent unauthorized access .
- 2. Encryption : Encrypting the data transmitted between the client and server to protect it from eavesdropping .
- 3. Data Integrity : Ensuring that the transmitted data is not altered or corrupted during the communication .
- 4. Forward Secrecy : Generating unique session keys for each connection , so that even if one session key is compromised, the data from previous sessions remains secure .
- 5. Key Exchange : Using secure mechanisms to exchange encryption keys between the client and server .
Overall, TLS plays a critical role in ensuring the confidentiality, integrity, and authenticity of data transmitted over the internet. It is widely used in applications such as online banking, e-commerce, and secure email communication .
In conclusion, TLS is an essential protocol for secure communication online. By implementing authentication , encryption , data integrity, forward secrecy, and secure key exchange , TLS can provide a robust security layer for internet communication .
1. Use strong cryptographic algorithms
TLS (Transport Layer Security) is a cryptographic protocol that provides secure communication over a network. It is widely used to secure online transactions, such as e-commerce websites and online banking.
TLS uses a combination of symmetric and asymmetric encryption algorithms to establish a secure connection between a client and a server . The symmetric encryption algorithm is used for bulk data encryption , while the asymmetric encryption algorithm is used for key exchange and authentication .
The TLS protocol uses various cryptographic algorithms, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) , to encrypt and protect the data during transmission . These algorithms provide strong ciphers that ensure the confidentiality, integrity, and authenticity of the communication .
Confidentiality means that the data is encrypted and cannot be read by unauthorized parties . The encryption ensures that even if an attacker intercepts the data, they will not be able to understand or use it.
Integrity means that the data cannot be tampered with during transmission . If the data is altered or modified by an attacker , the recipient will be able to detect it and reject the modified data.
Authenticity means that the communication is secure and trusted. The client and server verify each other’s identity using digital certificates , which are issued by trusted third-party authorities.
The use of strong ciphers in TLS is crucial to protect against attacks , such as brute-force attacks and man-in-the-middle attacks . Brute-force attacks involve trying all possible combinations of encryption keys to decrypt the data, while man-in-the-middle attacks involve intercepting and altering the communication between the client and server .
By using strong ciphers, such as AES-256 and RSA-2048, TLS ensures that the encrypted data remains secure and protected from these types of attacks . Additionally, TLS supports perfect forward secrecy , which means that even if the encryption keys are compromised in the future, the past communication cannot be decrypted.
Comparison of TLS versions:
| TLS Version | Cipher Suites | Key Exchange Algorithms | Supported Protocols |
|---|---|---|---|
| TLS 1.2 | AES, RC4, 3DES | RSA, Diffie-Hellman, ECDH | TLSv1.2, SSLv3 |
| TLS 1.3 | AES-GCM, ChaCha20-Poly1305 | DHE, ECDHE | TLSv1.3 |
Overall, TLS is a crucial security protocol that provides confidentiality, integrity, and authenticity of communication over a network. By using strong ciphers and supporting the latest versions of TLS, organizations can ensure that their data remains secure and protected .
2. Implement strong key exchange protocols
In the context of TLS (Transport Layer Security), the key exchange process is of paramount importance. It is a critical step that involves the secure exchange of encryption and decryption keys. The implementation of robust key exchange protocols is crucial to ensure the confidentiality and integrity of the exchanged keys.
3. Validating Digital Certificates
When it comes to TLS, digital certificates play a crucial role in authenticating the identities of both the server and the client . It is imperative to properly validate these certificates to establish a secure and trusted communication channel. Failing to validate certificates can expose the system to potential man-in-the-middle attacks , especially when dealing with invalid or expired certificates .
4. Protect against known vulnerabilities
Developers should stay updated with the latest security vulnerabilities and patch any known vulnerabilities in their TLS implementation. Regularly updating the TLS software and implementing necessary security measures helps protect against potential attacks .
As a technical specialist, it is crucial for developers to keep themselves informed about the latest security vulnerabilities in the TLS protocol and promptly address any known vulnerabilities in their implementation. Regular updates to the TLS software and the implementation of appropriate security measures are vital in order to safeguard against potential attacks .
By staying current with the latest security threats and vulnerabilities, developers can minimize the risk of unauthorized access to sensitive data and prevent any potential breaches of privacy. Regular monitoring and updating of the TLS software ensure that any identified vulnerabilities are promptly addressed and patched, preventing exploitation by malicious actors.
Implementing necessary security measures, such as encryption and secure coding practices, further enhances the overall security posture of the TLS implementation. By following best practices and industry standards, developers can significantly reduce the risk of unauthorized access and data manipulation.
Furthermore, it is important for developers to regularly evaluate the overall security of their TLS implementation and conduct thorough security assessments. This includes assessing the robustness of encryption algorithms, the strength of cryptographic keys, and the integrity of digital certificates .
A comparison of different TLS software and libraries can also be helpful in selecting the most secure and up-to-date solution. This can be done by considering factors such as the software’s track record in addressing security vulnerabilities, the frequency of updates , and the level of community support.
In conclusion, developers should prioritize staying updated with the latest security vulnerabilities and promptly patch any known vulnerabilities in their TLS implementation. Regular updates and the implementation of necessary security measures are essential for protecting against potential attacks and safeguarding sensitive data.
5. Enable HTTPS for secure communication
HTTPS: HTTP Secure
HTTPS, or HTTP Secure, is an extension of the HTTP protocol that uses TLS/SSL to secure the data transmitted between the client and the server . This protocol ensures that the communication is encrypted and protected from eavesdropping .
6. Follow best practices for secure configuration
Adhering to best practices for configuring TLS, such as disabling weak cyphers and using secure protocols , is crucial for enhancing the security of the communication . It is imperative to properly configure TLS to protect against potential vulnerabilities.
In conclusion, ensuring the security of Transport Layer Security entails using strong cryptographic algorithms, implementing secure key exchange protocols , validating digital certificates , protecting against known vulnerabilities, enabling HTTPS, and following best practices for secure configuration. By taking these measures, the privacy and confidentiality of the communication can be preserved, establishing a secure and trustworthy environment for data transmission .